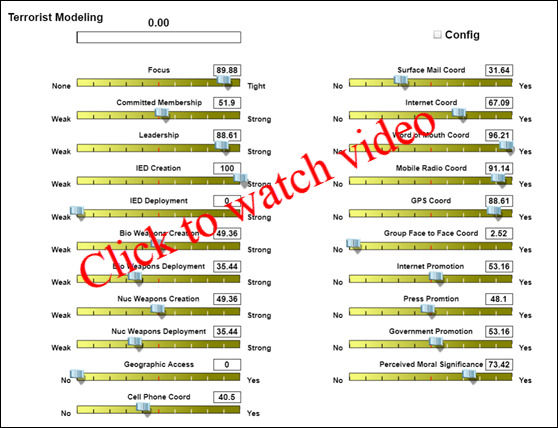

Scroll bars allow the user to identify "values" for a number of characteristics that might be used to define a terrorist group and their capabilities to target a specific target. In a real world application, this information might come from human operators, or from a database.
A Config Check Box in the upper right of the screen allows the display of a separate set of configuration parameters. The user can adjust the impact of a number of the characteristics of the model.
The output of this simple model is a "Relevance" bar and associated Risk Number (to the right of the title) that suggests how relevant a particular group (with its identified capabilities) is to the particular target identified by a geographic access and focus of the group. NOTE: When the model is first loaded, the "relevance" bar indicates 0 because Geographic Access of the group is set to No.
In a real world application, a geographic display might be animated to show the risk of potential targets by specific terrorist groups. The display would change automatically as the political environment changed, as the economy changed, as the potential targets changed, as groups changed, as the weapons available to the groups changed, etc.
NOTE: This demonstration can be made available as a stand-alone Windows .exe application to selective organizations with a direct request to Compsim.
Create a model of a terrorist group and suggest their relevance to a specific target.
Identify the Drivers to determine Relevance in an abstract way. Then identify the Inputs (measurements) that contribute to the Drivers. Finally refine how the input data is integrated to control the Relevance. All work to be done within the KEEL Toolkit using the "KEEL dynamic graphical language".
In the model created, "Perceived Moral Significance" was used to amplify the significance of "Committed Membership". The thought was that religious fundamentalism might be an added driver to perform terrorist acts (beyond just a general occupational act of being a terrorist). A configuration parameter sets a bottom level of control for Committed Membership (such that a general terrorist would still carry a base level impact to be integrated with Focus).
Committed Membership and Focus were combined to control the Amplitude of Relevance. The belief is that (collectively) these inputs could lead to the determination and intensity of the group.
Leadership was modeled such that strong leadership can amplify the potential for success, while weak, or non-existent leadership could detract from the potential for success. A configuration parameter allows the control of the significance of Leadership in the overall model.
Weapon creation and deployment capabilities for each of IED, Bio Weapons, and Nuclear were integrated in the same way. If the group could make the weapons, but could not deploy them, or if they had the means to deploy them, but could not make them, then the effect is that they could not be effective. On the other hand, if they could both make them and deploy them fully, they would be the most effective. Configuration parameters allow individual control of the significance of IED, Bio, and Nuclear capabilities when they are integrated in the overall model.
Geographic Access to the target is assumed to be mandatory for an attack to be carried out. Therefore the model was created such that no access means no relevance. Maximum access means maximum potential relevance.
Coordination capabilities can amplify relevance. The limits to how much is controlled by a configuration parameter. A number of individual coordination techniques are individually identified and collectively used to control the amplification of relevance.
Promotional capabilities can amplify relevance. The maximum impact is controlled by a configuration parameter. A number of individual promotional techniques are individually identified and collectively used to control the amplification of relevance.
The model, the way it is described above, took approximately 1 hour to create with limited testing.
Views allow just portions of the design to be displayed. This is helpful at times to allow the user to focus on just subsets of the overall design. A number of different "views" of the model were created: Config: Shows just the configuration values used to establish the impacts of different inputs. Leadership: Shows just the logic associated with Leadership, including its importance configuration. Allows the user to interact with this view and observe its impact on overall relevance. Tech Capabilities: Shows logic associated with IED, Bio Weapons, and Nuclear Weapons and associated configuration settings. Allows the user to interact with this view and observe its impact on overall relevance. RunWithConfig: Shows all of the inputs with configuration controls and hides all of the intermediate logic. Allows the user to manipulate / graph everything. Run Only: Shows just the runtime inputs so the user can manipulate the model. Configuration parameters are hidden to save space.
This design uses only linear integration techniques. For example the impact of Nuclear Deployment capabilities is demonstrated as a linear function. It could be that a non-linear view would be appropriate if one was considering the impact on a city, versus a nation. This can easily be defined within KEEL technology.
This design also uses some input variables that are not necessarily published facts. It is likely that they would be derived from various other pieces of information. A more complete system would be a hierarchy of information integrated to some decision or action at the top. KEEL can easily integrate information at multiple levels. It would be just like asking a human to establish a value for leadership. The leadership value would be determined by integrating a number of factors to determine the leadership value. KEEL makes this easy to develop.
This model only focuses on "Relevance" toward a specific target, assuming the target is identified.
Other situations might be modeled such as:
This model could easily be integrated into a broader real-time simulation. For example, depending on the intelligence, it could be integrated with the Yerkes-Dodson model and the Human Event Profiling to profile the action of the group in a dynamic environment. The group might transition from Un-engaged Defensive, to Un-engaged Aggressive, to Engaged Aggressive.... This will allow an organization to model the behavior of a specific group in realistic battlefield simulations.
This was a simple test case. No domain expertise exists at Compsim to develop these types of models. It was developed to show the simplicity of developing these types of models from a low cost standpoint. We suggest that domain experts can create these models without requiring the support of mathematicians or software engineers.
We also suggest that no domain expert, no matter how knowledgeable they are about the subject, will create the perfect model the first time. The model will evolve over time and require periodic updates as group behavior change. Only tools that allow "easy" access for updates and extensions will be economically feasible. KEEL provides this "easy to use" support such that the behavioral models can be created without the need for the specific skills of mathematicians or software engineers.
Compsim is a small R&D company focused on developing and licensing KEEL Technology. Compsim does not develop or license "products". Licensees of KEEL Technology should use it to create a competitive advantage in their market. Licensees of KEEL Technology get access to KEEL "tools" along with the rights to use the processing model.
KEEL is:
|
Copyright , Compsim LLC, All rights reserved |