
It's not just cute little balls flying around.It's the 100% auditable policies that describe how an automated system may decide how to interpret collateral damage when attacking a target. It is interpreting information in a new way. |
|
|
It's using "KEEL Technology" to determine "what to do and how to do it". |
Policies are provided to describe the rules of behavior when encountering a situation. In this case we are demonstrating the policy for a UCAV (Unmanned Combat Aerial Vehicle), regarding how it is to determine whether a target should be attacked and destroyed. The policy for interpreting the situation is described with the KEEL dynamic graphical language and deployed in the UCAV. The UCAV may have multiple policies in operation at the same time. This demonstration focuses on a single policy to evaluate its situation and determine if and when the target should be attacked.
In this demonstration, it is assumed that the UCAV has access to GPS data of the territory with known infrastructure (type and location). It also assumes that it is receiving constantly updated information from its own sensors and distributed intelligence systems that provide information on the location and importance of targets, as well as information on noncombatants and friendly forces. This information is being displayed graphically in the demonstration. For this demonstration, the policies control the application of force. The importance of the Target plays a significant role in the decision. The UCAV is also concerned with the potential impact on friendly forces, noncombatants, and infrastructure. A very important target (WMD), may justify some collateral damage. The policy described with the KEEL dynamic graphical language is explicit, allowing it to be monitored and audited. The policy described in this demonstration is for demonstration purposes only and is not suggested as one that would ever be deployed.

Each time the demonstration is started, 8 infrastructure components (utilities, political buildings, religious sites...) are randomly distributed on the map (indicated with a yellow circle with an "I" in the middle). Their significance is also randomly defined and shown by the size of the circle. The infrastructure elements remain stationary during each run of the demonstration. There are 7 noncombatant groups (indicated with a purple circle with an "N" in the middle). The size of the group is randomly created and shown by the size of the circle. These groups move throughout the demonstration. There are 8 friendly force units distributed randomly on the map when the demonstration starts (indicated with a green circle with an "F" in the middle). The size of each element is an indication of the number of friendly forces and is shown by the size of each circle. There are 4 enemy targets in this demonstration (indicated by the circle with a "T" in the middle). The size of the target is an indication of the target's importance. In this demonstration, the importance of the target changes throughout the demonstration to provide additional insight into the policy interpretation. In this demonstration, the Target is colored Gray when it is within range of collateral damage and it is not considered acceptable for attacking. The Target turns RED when it is acceptable for attacking, according to the evaluation of the other pieces of information by the KEEL Engine in the UCAV.
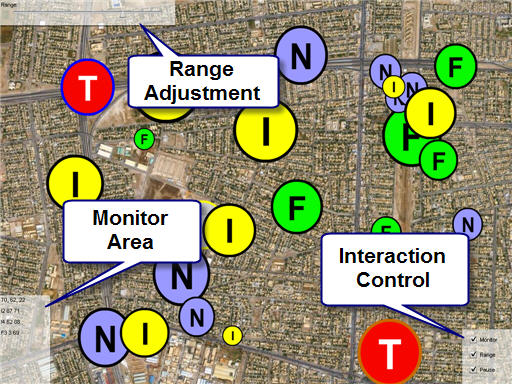
The lower right corner of the map has 3 checkboxes that enables some control over the demonstration. The Monitor checkbox opens a Monitor Area in the lower left corner of the map. The Range checkbox opens a Range configuration area in the upper left corner of the map. The Pause checkbox pauses the motion of the items to enable a "human" to observe and understand what is going on by looking at the monitor.

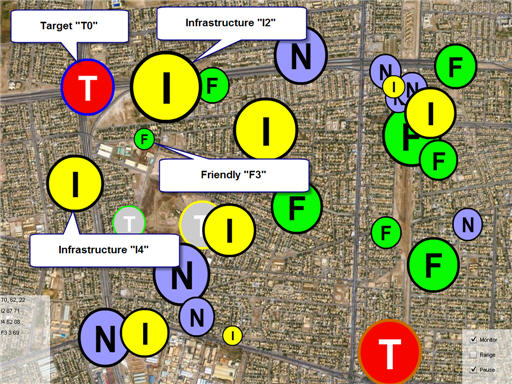
The image below shows the selection of the Monitor checkbox. By default, the target identified as "T0" is selected for monitoring. This is the target with the blue ring around it. The image below also shows that the system has been "paused", allowing us to capture a screen shot and describe what is going on.
When the Monitor check box is selected, the Monitoring Area is opened in the lower left corner of the display.
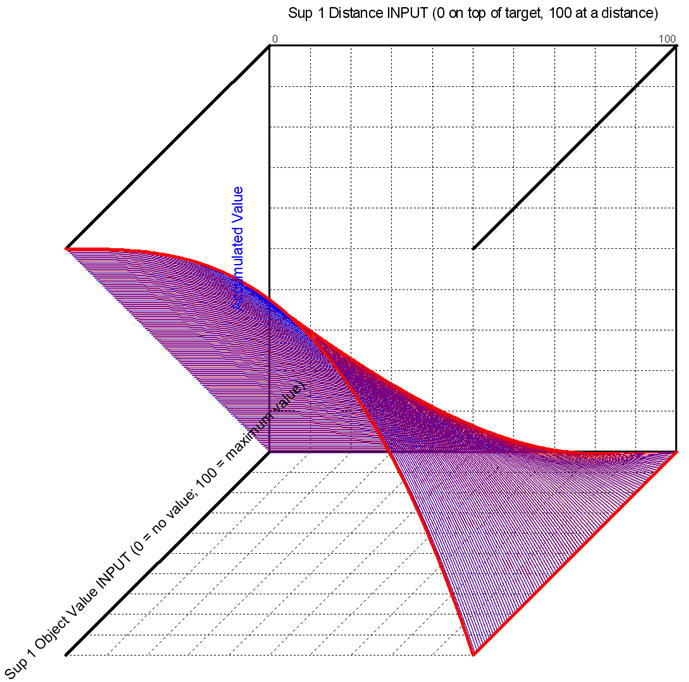
The top line of the Monitoring Area describes the Target. The name of the target is shown ("T0" in this case) followed by two numbers (62 and 22) in this case. The first number (62) represents the perceived importance of the target. This would be based on intelligence or sensor data (potentially integrated with another KEEL engine). The second number (22) represents the result of the KEEL integration of Target value with potential collateral damage from nearby objects (infrastructure items, noncombatant groups, and friendly force groups) at an instant in time. This resulting "adjusted value" is used to determine if the target is available for attack according to the KEEL defined policy. A threshold is set in this policy that requires the target to have an adjusted value of over 20 for it to be attacked.
The lines below the Target Line describe the items within range that may be damaged in the attack. This doesn't mean that they would be destroyed, but they may have some damage, depending on how far they are from the target. Each of the objects within range will be described with their identifying name, their value, and their normalized range value. For infrastructure items they will have an "I" followed by a numeric identifier. For noncombatant groups they will have an "N" followed by a numeric identifier. For friendly force groups, they will have an "F" followed by a numeric identifier.
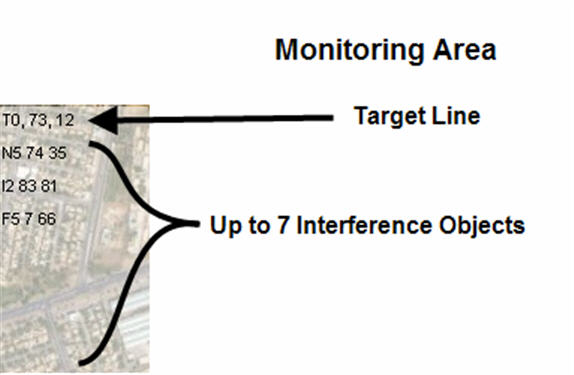
The image above shows that there are three objects within range: Noncombatant item "N5" with a value of 74 and distance of 35, Infrastructure item "I2" with a value of 83 and distance 81, and Friendly Force Group "F5" with a value of 7 and a distance of 66. The Target ("T0") was valued at 73 (out of 100). Integrating the collateral damage yields an accumulated value of 12.
By dragging the objects near the target closer to, or away from, the target, you will observe how the accumulated value changes. Dragging the target around you will see how the range of the objects change for integration into the accumulate value.
The Range is used to calculate the impact of the attack on surrounding objects. There are several ways this could be used. If the UCAV had different weapon systems that could be used to attack the target, each type may have a different impact area. Since all information is integrated together in a KEEL engine, the targets could always be analyzed while considering how each weapon system might impact collateral damage.
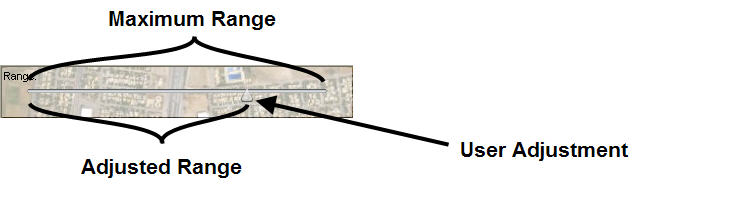
In this demonstration, the user can change the range impact. If the system is "paused", the range can be changed and you can observe the impact in the Monitoring area, and also observe how the range impacts which targets are available, and when they are available.
The KEEL "dynamic graphical language" is very effective in describing non-linear behavior. In this demonstration, a curve is used to describe how the collateral damage will be reduced as the distance between the target and the other objects increases. Since we are considering the impact of collateral damage on multiple objects to calculate an accumulated cost, we are constantly performing cost / benefit analysis (cost being collateral damage, and benefit being the value of eliminating the target). In a perfect battle, one would always like to destroy the target and avoid all collateral damage. Using conventional IF | THEN | ELSE logic, it would be easy to define a policy that said that if anything was in range of the target that was not to be damaged, then do not attack. The enemy would quickly realize that this policy could keep them safe by holding a single hostage. In the real world, everything is a balancing act. With KEEL, the policy is explicit. When UCAVs are being mass produced and are fighting the battles, it will be important that they are interpreting explicit policies.
This is a demonstration of how KEEL Technology can be used for adaptive targeting. It is not intended to suggest that this policy is correct or appropriate for this application. This architecture model is also just a demonstration. Other filtering methods may be more appropriate to selectively identify specific items for evaluation.
KEEL Technology provides a unique way to describe how to interpret information and how to act on that information in an explicit way. It is especially valuable when the interpretation of data involves integrating dynamically changing data items that possess complex inter-relationships that would otherwise be difficult or impossible to define.
|
Copyright , Compsim LLC, All rights reserved |